Log
Below are examples to configure strategies related to logs in Alarm Strategy Configuration:
- Application ID: enter the application name or the name of war package
- Specify the log: specify the full-path file name of the log
Triggering condition: the triggering condition shall be
- content: =XXX, indicating that the log contains XXX
- content! =XXX, indicating that the log does not contain XXX
Example: Alarm for network timeout
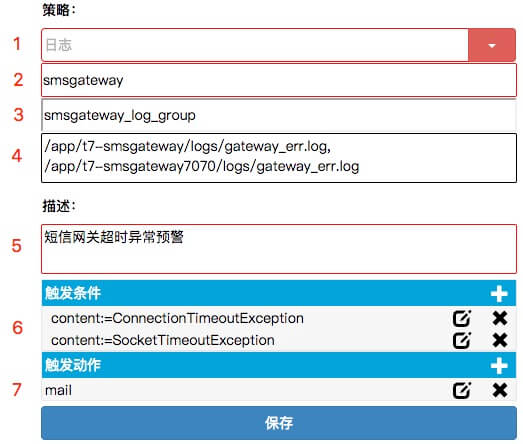
This example is an alarm strategy configured for the timeout of the carrier network by SMS gateway
- The alarm strategy is log
- This log strategy is configured for the application named as smsgateway
- Enter a group name if the strategy is configured for multiple log files
- Specify the log files of /app/t7-smsgateway/logs/gateway_err.log and /app/t7-smsgateway7070/logs/gateway_err.log
- Describe the alarm strategy for query
- The triggering condition is that the field ConnectionTimeoutException or SocketTimeoutException is detected in logs. Both exceptions can reflect the timeout in building connections or reading data
- Email alarm notification shall be sent out to the SMS operation department once the alarm strategy is triggered.