LDAP
The access permission of UAV is realized via LDAP. OPENLDAP is recommended. Please refer to http://www.openldap.org/ for OpenLDAP installation
Correspondence between UAV Access Permission and LDAP Access Permission
Below is the LDAP structure in general
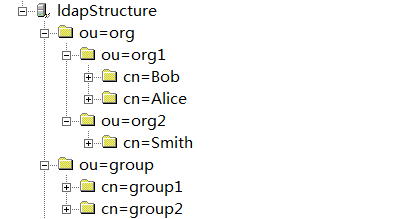
Generally, a member belongs to one specific organization only in the organization chart. At the same time, a member may belong to multiple business groups.
Signin Permission
Sign in UAV AppHub with the domain account of LDAP. The domain account is linked with a unique property of the member. The property name can is configurable.
Application Access Permission
The organization authorizes the access permission to applications in UAV AppHub. Members of an organization can access several specified applications. Groups authorized to access AppHub are named in the format of org/org1.
Access Permission to Data of Application Groups
The business group authorizes the access permission to data of application groups, such as application monitoring and application group monitoring. Members of the same business group are allowed to access several specified application groups. Business groups authorized to access AppHub are named in the format of group1.
The relationship between the members and the business groups are defined by the field “memberOf” (configurable). For example, the memberOf property of the node Bob is cn=group1,ou=group,dc=my-domain,dc=com, indicating that Bob belongs to group1. The member node may have several memberOf fields. The business group requires member field (configurable) to display its membership. For instance, the member property of the node group1 is cn=Bob,ou=org1,ou=org,dc=my-domain,dc=com, indicating that Bob is a member of group1.
Add properties of custom business group to members to illustrate the belongingness relations, if there is no business groups in LDAP. For example, add MyGroup to the node Smith and authorize MyGroup in AppHub for access control.
LDAP Configuration
The field for LDAP configuration in AppHub Configuration is uav.apphub.sso.ldap.connection.info, with its value being a json character string as below
{"url":" ldap://127.0.0.1:389/","loginbasedn":" dc=my-domain,dc=com","querybasedn":" dc=my-domain,dc=com","user":" admin","password":" admin","suffix":" @creditease.cn","primaryKey":" userPrincipalName","groupKey":" memberOf","groupTag":" mailGroup","memberKey":" member","groupQueryField":" mail","userQueryField":" mail"}
Below is the illustration of the field components
- url: LDAP address
- loginbasedn: sign in basedn (top DN in the organization structure)
- querybasedn: query basedn (including the DN for the organization structure and the DN for nodes of business groups)
- user: user name of the administrator in LDAP
- password:password of the administrator in LDAP
- suffix: uniform suffix of domain account (null character string if none)
- primaryKey: property of the member who signs in the domain account
- groupKey: property of custom business groups (memberOf by default)
- groupTag: field that should be included in the properties of business groups (null character string if none)
- memberKey: custom property of members (member by default)
- groupQueryField: query property of business groups (for information query)
- userQueryField: query property of members (for information query)
UAV Access Permission Extension
UAV provides the interfaces for custom extension of access permissions. In addition to LDAP, access permission can also be realized by adding the implementation class of GUISSOClient under Abstract class into com.creditease.uav.apphub.sso of com.creditease.uav.console, thus realizing abstract access validation. Then change uav.apphub.sso.implclass into the full class name of the custom implementation class in AppHub configuration.